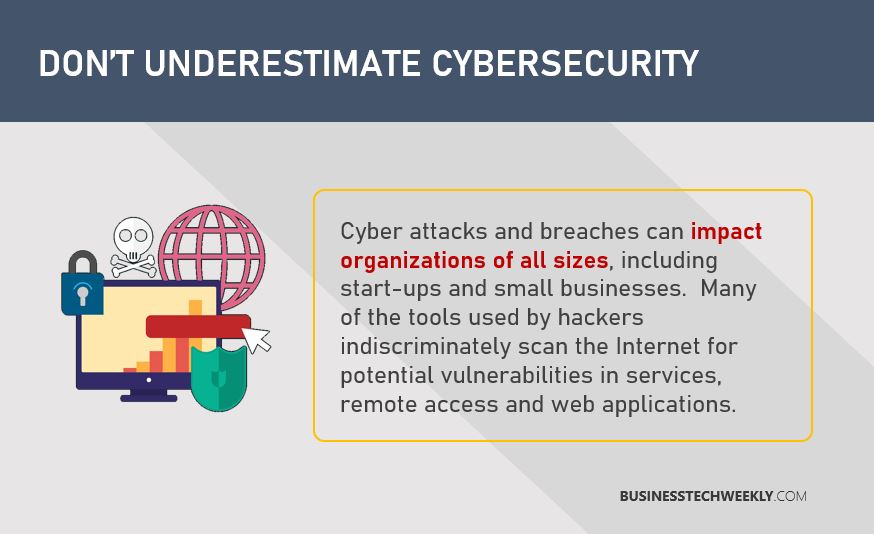
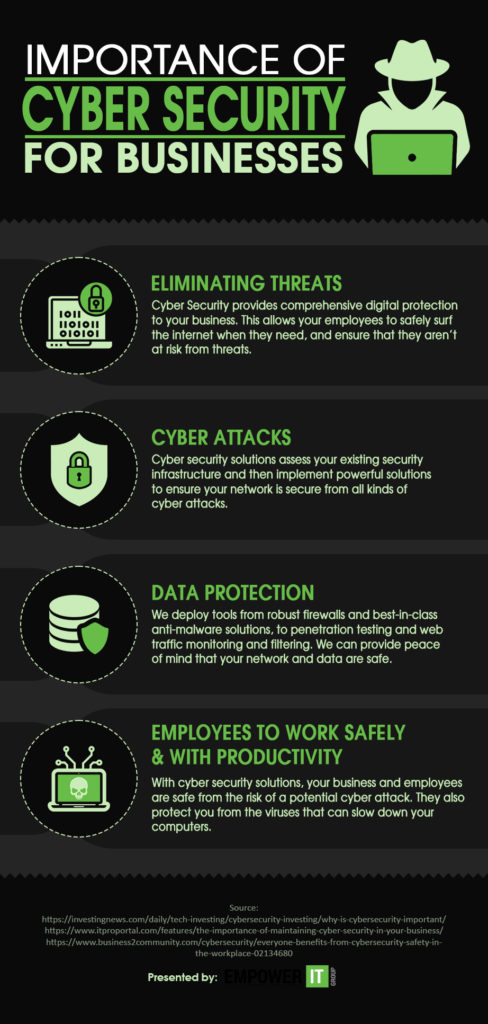
Real Info About How To Protect Data From Potential Threats

For backup, it staff standardized on ibm’s tivoli storage manager.
How to protect data from potential threats. Educate them on the latest threats and how to identify phishing. Mobile devices, tablets and laptops that are connected to corporate networks give. Most companies let you choose what should or should not be.
Use network protection measures protecting your network is crucial. How can it help monitor vast amounts of public data for potential threats. With more global locations & advanced features, vultr provides better performance than do.
Microsoft recommends you choose passwords that are “unique, long and strong.” it also recommends you keep your passwords to yourself, no matter how much it’s killing you. Install a firewall ensure proper access controls use ids/ips to track. You don’t have to start from scratch;
Endpoint protection protects networks that are remotely bridged to devices. Make sure your employees are aware of the importance of cybersecurity and the steps they need to take to protect your data. Implementing a policy on strong user passwords is critical to data protection.
As long as we are vigilant and aware of how to protect ourselves from threats, we can rest assured that our money and assets are protected. Think of protection as your data army, standing. If you want to eliminate threats to your data, start with risk management as soon as possible.
Tune up your privacy settings. Simplify your network performance monitoring & troubleshooting. Ad are you concerned with the risk of a security breach in a changing landscape of threats?
Continuously monitoring your brand will help to protect your brand from various infringement practices like. To keep your network and its traffic secured: Consider using a new browser, such as firefox,.
Use reliable antivirus software installing an antivirus software. Awareness programs to educate users about insider threats. Deploying an intrusion detection and prevention system (ids/ips) that provides deep.
You leave a data trail every time you use products like facebook and google. Spam filters can block traffic based on global threat dictionaries. Depending on the network you use in your business, there are particular systems you can use as protection.
Ad protect all data and assets with this single, unified solution from kyndryl. Start a secure free trial.







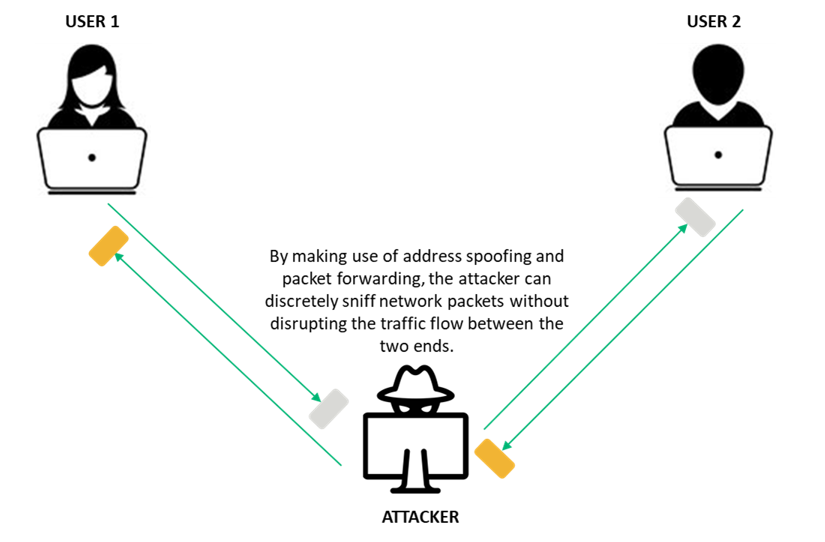

![Infographic] The 4 Biggest Cyber Security Risks Your Business Faces And How To Beat Them - Exemplify - More Than A Master Agent](https://www.exemplifygroup.com/wp-content/uploads/2018/10/exemplify_infographic_100418.jpg)